
Dynamic Asset Inventory
Legacy inventories are fragmented and reactive.Omny gives you real-time, connected visibility across IT, OT, and physical environments so you can act with precision.
Making your inventory work for you.
More than static PDFs—Omny turns assessments, network diagrams, and compliance documentation into collaborative, always-current artifacts. Easily update, version, and share insights across engineering, security, and operations teams.
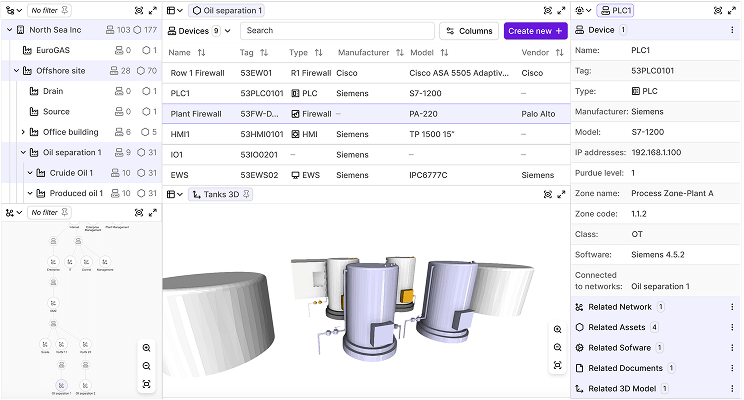
Consolidated inventory
Omny replaces spreadsheets and siloed tools with a real-time, hierarchical view of your entire cyber-physical landscape.- Functional asset mapping (e.g., welding machines, packaging systems) linked to operational roles
- Device-level attributes like IP addresses, firmware, and physical location
- Unified model across IT, OT, and physical infrastructure

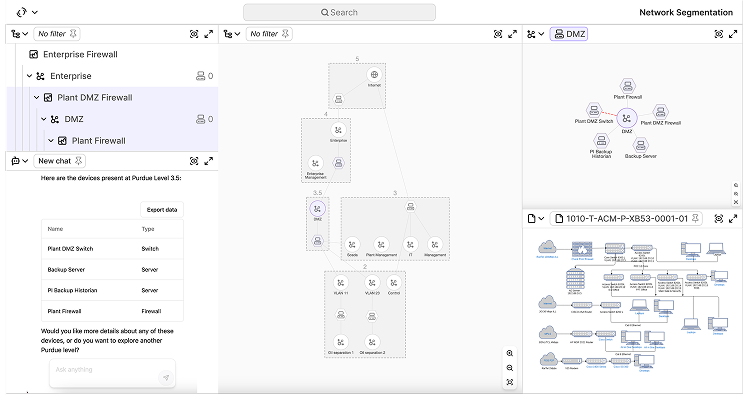
Network diagrams and segmentation mapping
Omny dynamically maps connections across systems and shows where segmentation succeeds or fails.- Automated network diagrams across IT and OT layers
- Zones and conduits mapped per ISA/IEC 62443 standards
- Traffic paths and boundary visualization to validate security controls

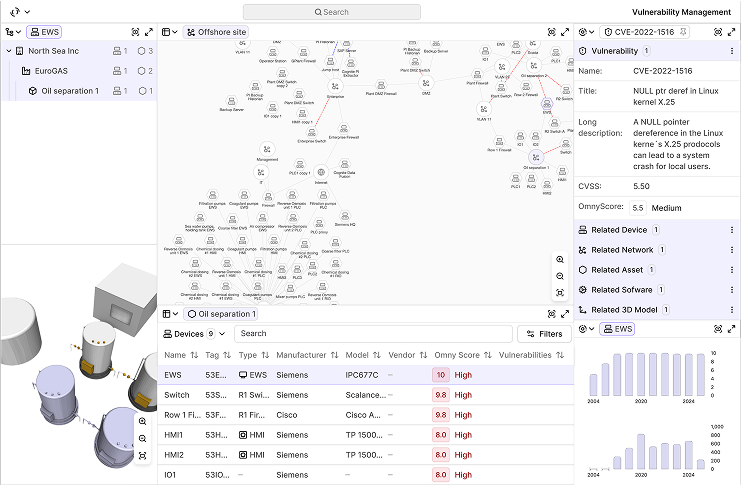
Vulnerability assessment
Vulnerability lists are overwhelming without context. Omny connects each CVE to operational impact—then scores the risk based on exposure, criticality, and control coverage.
- Mapped CVEs from NIST to specific devices
- Omny Score from 0 (secure) to 10 (high risk), factoring in role and network placement
- Prioritized remediation guidance tied to operational relevance

Meet the Omny Platform
Gain insight into your data with the ability to see and analyze in one platform.
 Consolidated Inventory
Consolidated Inventory
- Functional asset mapping (e.g., welding machines, packaging systems) linked to operational roles
- Unified model across IT, OT, and physical infrastructure
- Device-level attributes like IP addresses, firmware, and physical location
 Network mapping and segmentation
Network mapping and segmentation
- Automated network diagrams across IT and OT layers
- Zones and conduits mapped per ISA/IEC 62443 standards
- Traffic paths and boundary visualization to validate security controls
 Vulnerability assessment
Vulnerability assessment
- Mapped CVEs from NIST to specific devices
- Omny Score from 0 (secure) to 10 (high risk), factoring in role and network placement
- Prioritized remediation guidance tied to operational relevance
See how this applies to your industry
Explore how Omny’s threat intelligence capabilities address sector-specific threats:



