
Threat Intelligence
See threats in context. Act on what matters. Omny gives you the visibility, speed, and confidence to move quickly from intel to action.
AI-Driven Threat Prioritization
Get real-time threat intelligence tailored to your industrial environment. Identify critical threats faster and guide action across security and operations.
Stop reading. Start responding
Most intel feeds overwhelm your team with noise. Omny filters what’s relevant, using AI to score threat actors by capability, motivation, and relevance to your environment.- Identify threats with the highest potential impact
- Prioritize based on your industry, geography, and asset exposure
- Backed by analyst-verified AI models

Built for industrial security teams.
Your threat landscape is unique. Your intel should be too. Omny enables you to create custom intelligence libraries using public data, internal sources, and third-party platforms—all in one place.- Centralized intel workspace with search and chat
- Ingest data from your threat intelligence platforms
- Organize by business relevance and operational context

Dynamic threat assessments
No more PDFs. No more guesswork. Omny replaces static reports with real-time assessments, network diagrams, and compliance documentation, shaping it into collaborative, always-current artifacts.
- Continuously updated threat scenarios
- Quantified impact aligned with your operational assets
- Easily share insight across engineering, security, and operations teams

Meet the Omny Platform
Gain insight into your data with the ability to see and analyze in one platform.
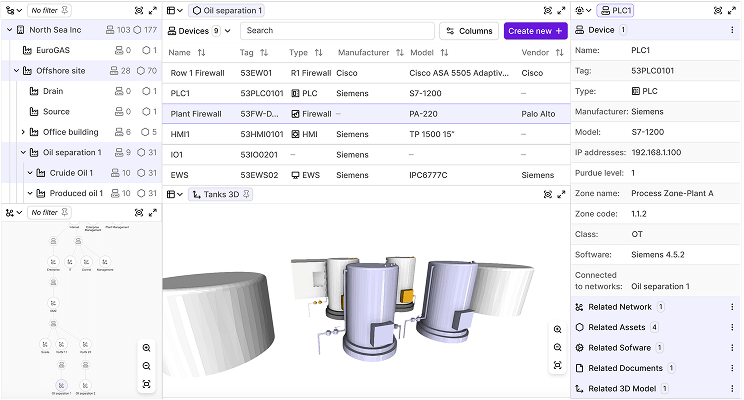
 Consolidated Inventory
Consolidated Inventory
- Functional asset mapping (e.g., welding machines, packaging systems) linked to operational roles
- Unified model across IT, OT, and physical infrastructure
- Device-level attributes like IP addresses, firmware, and physical location
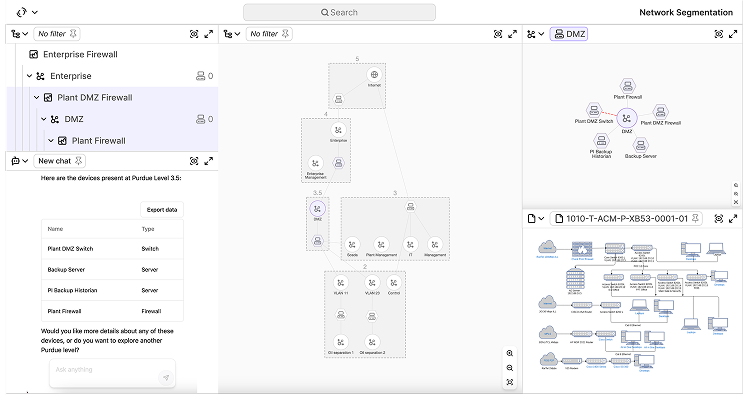
 Network mapping and segmentation
Network mapping and segmentation
- Automated network diagrams across IT and OT layers
- Zones and conduits mapped per ISA/IEC 62443 standards
- Traffic paths and boundary visualization to validate security controls
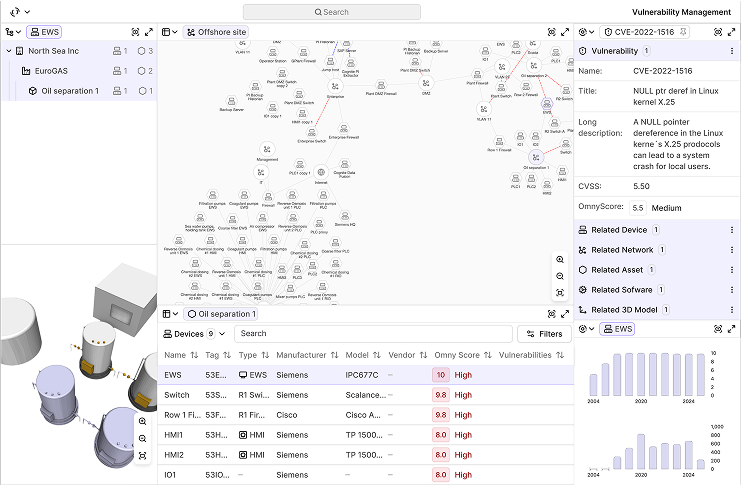
 Vulnerability assessment
Vulnerability assessment
- Mapped CVEs from NIST to specific devices
- Omny Score from 0 (secure) to 10 (high risk), factoring in role and network placement
- Prioritized remediation guidance tied to operational relevance
See how this applies to your industry
Explore how Omny’s threat intelligence capabilities address sector-specific threats:




